Which Network Is Least Secure?
Network security is an important aspect of any organization’s security defense plan. The security of a network can be measured by its ability to protect against malicious attacks, unauthorized access to data, and the ability to detect and respond quickly to threats. Unfortunately, some networks are inherently more secure than others, leaving organizations that use these networks more vulnerable to attack. The network security that is least secure is the open network, which is a public network that anyone can access without authentication. An open network is highly susceptible to attack because of its lack of authentication and encryption. This type of network is also vulnerable to eavesdropping, which can give attackers access to sensitive data and information. Additionally, open networks have limited control over the type of traffic they can support, making it easier for hackers to exploit vulnerabilities. Organizations should avoid open networks and instead opt for secured networks to ensure the safety of their data.
Types of Networks
As technology continues to become more sophisticated, the types of networks available to businesses and individuals are continuously changing. Each network type offers its own advantages and disadvantages, but when it comes to security, some networks are more secure than others. Knowing which network is best for your needs is essential for keeping your data secure.
The most common types of networks are wired and wireless. Wired networks use cables to connect devices, while wireless networks use radio waves. Wired networks are usually more secure than wireless networks because they are not prone to interference and are more difficult to access from outside sources. However, they can be more expensive to set up and maintain.
Another type of network is a virtual private network (VPN). A VPN uses encryption to protect data that is transferred over the internet. This makes it much more difficult for hackers to gain access to your data. VPNs are also relatively secure, but they can be expensive.
Finally, a cloud network is another type of network that is becoming increasingly popular. Cloud networks store data in the cloud, meaning it is stored on remote servers and not on physical devices. Cloud networks are usually secure, but they can be vulnerable to attacks if not properly configured.
No matter which network you choose, it’s important to understand the security risks associated with each type of network and take steps to protect your data. By choosing the right network for your needs, you can ensure that your data is secure and remain confident in your online security.
Security Threats
on Networks
As the world becomes increasingly interconnected, the threat landscape is also rapidly changing. With the emergence of new technologies, malicious actors have been able to exploit the vulnerabilities of networks. As businesses and individuals rely more and more on networks for communication, data storage, and other activities, it is essential to be aware of the security threats that exist on networks. From phishing scams to malware infections, there are a myriad of risks that can affect the security of networks.
When it comes to identifying which network is least secure, there is no definitive answer. Every network is vulnerable to attack and the security of each network depends on the measures taken to protect it. For example, wired networks are often more secure than wireless networks, since wireless networks are more accessible to attackers. Additionally, the underlying technology of a network can also affect its security; for instance, older networks that have not been updated to the latest security protocols can be more vulnerable.
When it comes to protecting networks from security threats, the best approach is to have a comprehensive security strategy that includes multiple layers of defense. This should include utilizing the latest security protocols, up-to-date firewalls, and strong password policies. Additionally, user education is also important, as teaching users how to recognize phishing attempts and other threats can help prevent malicious actors from penetrating networks. By taking these steps, organizations and individuals can ensure their networks are as secure as possible.
Network Security Solutions
In the digital age, the importance of network security cannot be overstated. Technology advances have enabled businesses to connect to a global network of customers and partners, opening up new opportunities for growth and success. But with the increased connectivity comes increased risk. Cybersecurity threats are constantly evolving, leaving businesses vulnerable to data breaches and other malicious activities. As such, it is essential for businesses to identify the least secure network and implement the right security solutions to mitigate the risks.
When selecting a network security solution, businesses should consider the security protocols it offers, such as firewalls, encryption, authentication, and access control. Additionally, the security solution should be able to monitor and detect any suspicious activity on the network and alert the necessary personnel for action. A comprehensive solution should also be able to provide different levels of access for different users and prevent unauthorized access.
To ensure that the network is as secure as possible, businesses should also regularly audit the security system and test the various security measures. This helps to identify potential vulnerabilities and take preventive measures such as patching and updating the system to make sure it is up to date with the latest security protocols. In addition, businesses should educate their employees on best practices for security, such as using strong passwords and not sharing confidential information.
Network security is an essential component for businesses of all sizes. By selecting the least secure network and implementing the right security solutions, businesses can protect their data and customers from malicious activities and ensure that their operations run smoothly.
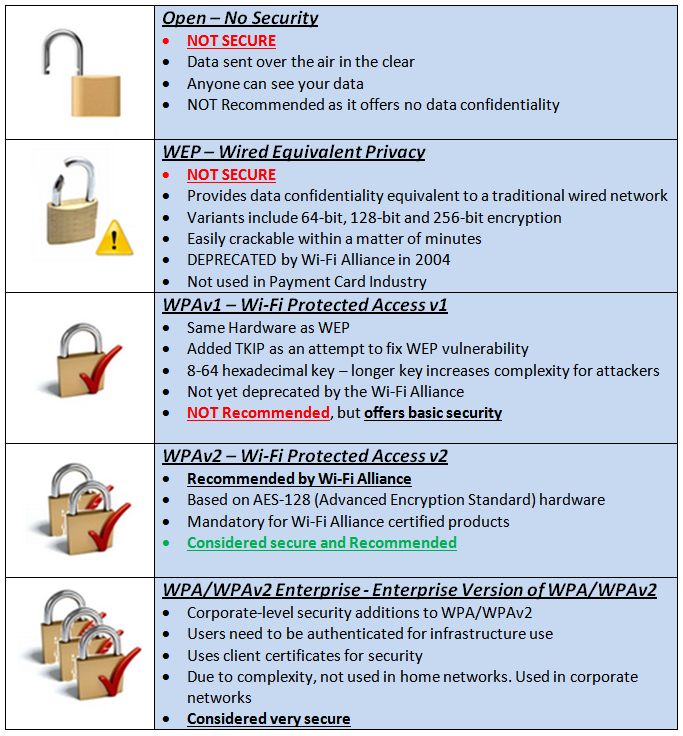
Weaknesses of Common Network Protocols
The internet is a vast network of connected devices, and the security of these networks rely on protocols to keep data secure. Unfortunately, not all network protocols are created equally, and some are more vulnerable to attack than others. In this blog, we’ll take a look at the weaknesses of some of the most commonly used network protocols and discuss which network is least secure.
First, let’s consider the Transmission Control Protocol (TCP). This protocol is used for reliable, connection-oriented communications between two devices on a network. However, the protocol is vulnerable to Denial of Service attacks, which can bring down a network or server by flooding it with requests.
Next, we have the User Datagram Protocol (UDP). Although UDP is more efficient than TCP, it is susceptible to spoofing. Spoofing is a technique used by attackers to send malicious messages that appear to come from a legitimate source.
Finally, we have the Internet Protocol (IP). IP is the most widely used network protocol, but it is also the least secure. IP is vulnerable to eavesdropping, which can allow attackers to intercept data as it is sent between two devices.
Overall, it is clear that IP is the least secure of the three protocols. Not only is it vulnerable to eavesdropping, but it also lacks the reliability and robustness of the other two protocols. To ensure maximum security, it is important to use protocols that offer a higher degree of protection.
Best Practices for Network Security
When it comes to network security, the best practices you should follow to ensure your network’s safety are essential. Implementing the right measures to protect your network from malicious intent can help keep your data secure and prevent cyberattackers from gaining access to your system. The most effective network security practices include firewalls, antivirus software, two-factor authentication, patch management, and user access control.
Firewalls are one of the most important network security measures, as they are the first line of defense against malicious activity. Firewalls prevent unauthorized access to your system by blocking certain types of packets, such as those from malicious sources. Antivirus software is also essential for protecting your network from viruses, Trojans, and other malicious software.
Two-factor authentication is another great security measure for networks. This type of authentication requires two pieces of information, such as a password and a one-time passcode, before access is granted. This helps protect against unauthorized access by adding an extra layer of security.
Patch management is also important for keeping your system secure. It involves regularly scanning for software updates and patches to ensure that your system has the latest security measures. Automating this process can help reduce the risk of security vulnerabilities.
Finally, user access control is also essential for network security. This involves setting up access rights for users so that they can only access certain parts of the network. This helps ensure that unauthorized users are not able to access sensitive information.
Overall, these security measures are essential for keeping your network secure and preventing malicious activity. Implementing the right network security practices can help ensure your data is safe from cyberattacks.
Conclusion
When it comes to security, the best network for you depends on the level of security you’re after and the type of data that you’re transferring. Public networks are generally less secure than private networks, while wireless connections may be more vulnerable to attack than wired ones. However, no network is entirely secure, and there are always ways to reduce the risk of a security breach. Consider factors such as encryption protocols, authentication methods, and access controls when evaluating network security to ensure that your data is as safe as possible.
FAQs About the Which Network Is Least Secure?
1. What makes a network less secure than others?
A network’s security is determined by its ability to protect its data and resources from unauthorized access, use, modification, destruction, or disruption. Networks which lack strong security measures such as encryption, authentication, and access control are considered to be less secure than those with these measures in place.
2. How can I tell if my network is secure or not?
You can check the security of your network by performing a vulnerability assessment. This will identify any potential weak points and security risks that could compromise the security of your network. Additionally, you should also use secure protocols such as SSL/TLS and IPSec when transmitting sensitive data, and ensure that all users have strong passwords.
3. What steps can I take to make my network more secure?
To make your network more secure, you should regularly update your security software and use a firewall to protect against incoming and outgoing threats. You should also restrict access to the network by using strong user authentication and authorization protocols such as two factor authentication. Additionally, you should encrypt data that is stored and transmitted on the network.
Conclusion
In conclusion, it is difficult to definitively determine which network is the least secure as there are many factors that can contribute to the security of a network. Some networks may be more vulnerable to malicious attacks or data breaches than others, depending on the size of the network, the type of security measures in place, and the level of user awareness. Ultimately, it is important for organizations to assess their security needs and implement the most appropriate security measures to protect their data and networks.