What Are Top 5 Key Elements Of An Information Security?
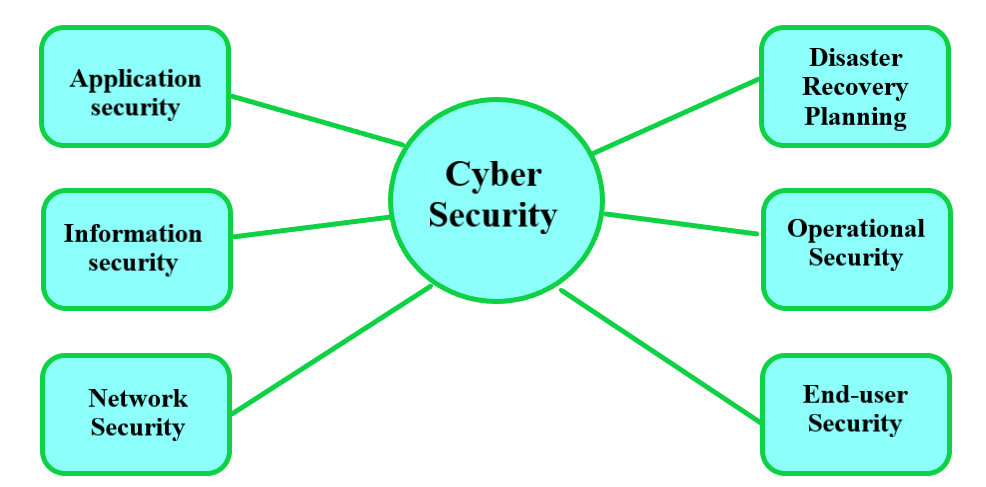
Information security is the protection of data and information systems from unauthorized access, use, modification, disclosure, or destruction. It is essential to ensure the security of information systems and the data they contain. The top 5 key elements of an information security system are:
1. Access Control: Access control is a fundamental element of information security, as it ensures that only authorized users can access data and systems.
2. Data Protection: Data protection is the process of protecting data from unauthorized access, modification, or destruction. This includes encryption and other measures to ensure that data is secure.
3. Network Security: Network security is the process of protecting an organization’s data and systems from external threats, such as hackers.
4. Risk Management: Risk management is the process of identifying and assessing potential risks and vulnerabilities, and taking steps to mitigate or eliminate them.
5. Incident Response: Incident response is the process of responding to and managing security incidents. This includes identifying the cause of the incident, mitigating the effects, and taking steps to prevent similar incidents from occurring in the future.
Understanding the Threat Landscape
The threat landscape is constantly changing and evolving, making it increasingly difficult for organizations to stay ahead of potential risks. Understanding the threat landscape is essential for any organization looking to protect its digital assets. It involves identifying the various types of threats that could affect an organization’s data and systems, such as malware, viruses, ransomware, and phishing attacks. Knowing the sources of these threats, as well as the potential impact they could have on the organization, is critical to developing a comprehensive security strategy. By understanding the threat landscape, organizations can better prepare for potential security incidents and ensure their systems remain secure.
Establishing a Robust Security Strategy
A robust security strategy is essential in today’s digital world. It involves the implementation of best practices and technologies to protect an organization’s critical assets from cyber threats. It is a comprehensive approach that is tailored to the organization’s unique needs and goals and should include the assessment and management of both physical and digital assets. A robust security strategy should also include the implementation of tools such as authentication, encryption, firewalls, intrusion prevention, and anti-malware protection. Additionally, the strategy should include policies and procedures to ensure proper security controls are in place, as well as the training of personnel to ensure they are aware of the risks and security measures that must be taken. By establishing a robust security strategy, organizations can protect their data and maintain the trust of their customers.
Deploying Effective Security Controls
The development of effective security controls is a critical part of any successful organization’s security strategy. Security controls provide the necessary structure and guidance for the implementation of appropriate security practices. They help organizations identify and mitigate risks while protecting data and resources. By deploying effective security controls, organizations ensure they have appropriate measures in place to protect their data, networks, and systems from malicious attacks and unauthorized access. These safeguards also ensure compliance with industry-specific regulations and standards. Security controls are an essential part of any organization’s security plans, and they should be regularly evaluated and updated to ensure they remain effective.

Monitoring and Responding to Threats
Monitoring and responding to threats is an essential part of keeping your business secure. By keeping an eye on what’s going on in your environment and responding quickly to any security threats, you can safeguard your assets and data against malicious actors. A well-thought-out monitoring and response plan can help you detect and mitigate potential threats before they cause damage to your systems or sensitive data. This plan should include regular scans and monitoring of your network and systems for any suspicious activity, as well as having processes in place to quickly respond to any threats that are detected. By proactively monitoring and responding to threats, you can help protect your business from becoming a victim of cybercrime.
Ensuring Data Privacy and Compliance
Data privacy and compliance is a critical component of modern business operations. It is important to ensure that all data collected and stored is secure and that the appropriate measures are taken to protect it. This includes making sure that any data collected is done so in accordance with all applicable laws and regulations, as well as that all appropriate security measures are taken to protect it from unauthorized access. It is also essential to ensure that any data shared with third parties is done so in a secure manner, and that any data stored on third-party systems is also protected. By taking the necessary steps to ensure data privacy and compliance, businesses can ensure that their data is safe and secure, and can remain compliant with all applicable laws and regulations.
Technology Solutions for Information Security
Technology solutions for information security are essential in today’s digital world. As the amount of data stored electronically continues to grow, the need for secure, reliable solutions becomes even more paramount. Information security solutions provide protection for sensitive data, preventing unauthorized access and safeguarding user privacy. These solutions can range from simple software solutions to complex hardware systems such as firewalls, encryption, and identity management. They provide a layer of defense for companies, ensuring that any data stored or transmitted online is secure and only accessible to authorized personnel. Additionally, these solutions can help companies comply with industry regulations and protect their reputation, as well as their customers, from data breaches.
FAQs About the What Are Top 5 Key Elements Of An Information Security?
Q1. What are the top 5 key elements of an information security system?
A1. The top 5 key elements of an information security system are: authentication, authorization, confidentiality, integrity, and availability.
Q2. How does each element help protect data?
A2. Authentication helps verify the identity of a user, authorization ensures users only have access to the resources they are authorized to access, confidentiality helps keep data secure from unauthorized access, integrity helps ensure data accuracy and completeness, and availability ensures the system is up and running when needed.
Q3. How can I ensure my information security system is up to date?
A3. You should regularly patch your system with the latest security updates, use strong passwords, use two-factor authentication when possible, and monitor your system for any suspicious activities. Additionally, you should stay up to date on the latest information security guidelines and best practices.
Conclusion
The top 5 key elements of an information security system are 1) confidentiality, 2) integrity, 3) availability, 4) authentication and 5) non-repudiation. All of these elements are essential for a secure, safe and reliable information system. Confidentiality ensures that the data and information is only accessible to authorized users; integrity ensures that the data and information is accurate and unaltered; availability ensures that users can access the data and information when needed; authentication verifies the identity of the user; and non-repudiation prevents the sender of the data from denying that they sent it. Implementing all of these elements into an information security system is essential for protecting data and information from unauthorized access, malicious attackers, and other security risks.