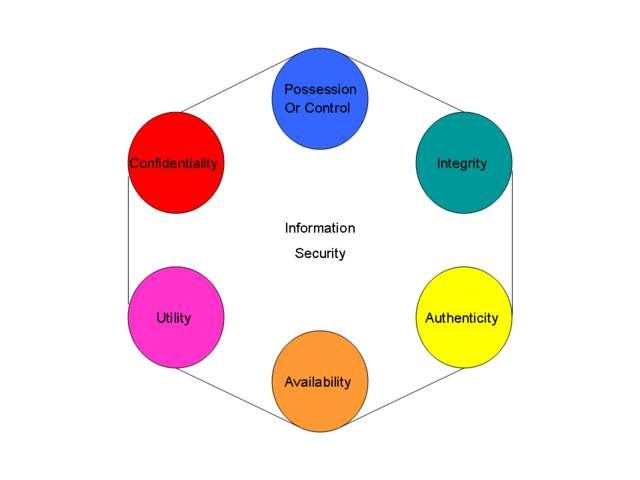
What Are The Six Components Of Information Security?
Information security is a critical aspect of any organization’s operations. It involves protecting data, systems, and networks from unauthorized access, destruction, and modification. The six components of information security are confidentiality, integrity, availability, authentication, authorization, and non repudiation. Each component is important in its own right and works together to provide a comprehensive security solution. Confidentiality ensures that only authorized personnel can access sensitive data. Integrity ensures that data is accurate and remains unchanged. Availability ensures that data and systems are available when needed. Authentication verifies the identity of users. Authorization grants access to resources based on identity. Finally, non repudiation ensures that an action or message cannot be denied or repudiated. Together, these components provide a comprehensive security solution that is essential for any organization.
Access Control
Access control is the process of limiting access to systems, networks, and other resources, which is essential in today’s world of increased security risks and threats. It is used to protect data and resources from unauthorized access, and is an important security measure in businesses and other organizations. Access control can be implemented in various ways, such as passwords, bio metrics, authentication tokens, and other methods. By implementing access control, organizations can ensure that only authorized personnel are able to access sensitive data, resources, and applications, and protect against malicious attacks.
Data Security
Data security is a critical component of any business operation, as it ensures that confidential customer data remains safe and secure. It involves the use of various security measures to protect data from unauthorized access and misuse. This includes encryption, authentication, access control, and data backup systems. To ensure data security, organizations must employ strong security policies and procedures, such as password protection, two-factor authentication, and regular security audits. By taking these steps, businesses can guarantee that their data is safe and secure, protecting customers and their own operations from malicious actors.
Risk Management
Risk Management is a critical component of any successful business strategy. It involves assessing potential risks to the organization and developing strategies to manage those risks. Risk management helps businesses to identify, assess, and prioritize potential risks and develop strategies to mitigate or prevent those risks. It is important to identify risks before they occur, and to have a plan for how to address them in the event they do. Risk management helps businesses to proactively identify and address potential risks, as well as keeping the organization safe from harm. With the right strategies and processes in place, risk management can help businesses to maximize profits and reduce losses.
Network Security
Network security is the practice of protecting networks, systems, and programs from digital attacks. Network security involves a set of strategies and tools to prevent unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Network security covers a variety of computer networks, such as private and public networks, including the internet. It includes both hardware and software technologies. It is important to ensure that the data going through a network is protected from malicious attacks and unauthorized access. Network security is vital to the safety of businesses, government agencies, and individuals. It helps to protect confidential data, prevents data loss, and keeps networks and systems secure.
Application Security
Application Security is an essential element of software development and deployment. It ensures that applications are secure from external threats and vulnerabilities, and that data is kept confidential and secure. Application Security also ensures that applications are free from malicious actors, and that data is not misused or compromised. Application Security is a vital component of any security strategy, and should be considered when developing and deploying applications. Application Security is an ongoing process, as threats and vulnerabilities evolve. It requires proactive measures, such as regular maintenance, patching, and security testing, to ensure that applications remain secure and protected from malicious actors. Application Security is key to protecting data, systems, users, and organizations from unauthorized access or malicious actors.
End-User Education
End-User Education is a key component of any successful IT system. It ensures that all end-users are adequately trained on how to use the system, allowing them to make the most out of it. End-User Education provides users with the skills and knowledge they need to be productive and efficient. It also helps to reduce the risk of data loss or security breaches due to user error. By equipping users with the knowledge and understanding of how to navigate and use the system, they can make the most of their IT investment. End-User Education is an essential investment for any IT system and can provide a significant return on investment.
FAQs About the What Are The Six Components Of Information Security?
Q1: What are the six components of Information Security?
A1: The six components of Information Security are Confidentiality, Integrity, Authentication, Availability, Non-repudiation, and Authorization.
Q2: What does each component of Information Security do?
A2: Confidentiality ensures that data is only accessible to authorized individuals. Integrity ensures accuracy and completeness of data. Authentication verifies the identity of users. Availability ensures that data and services are accessible when needed. Non-repudiation prevents denial of actions. Authorization grants users access to resources.
Q3: How can these components of Information Security be implemented?
A3: These components of Information Security can be implemented through the use of policies, procedures, and technologies such as encryption, firewalls, and authentication tools. It is important to ensure that all components are implemented in order to provide a secure environment.
Conclusion
In conclusion, the six components of information security are confidentiality, integrity, availability, authentication, authorization, and non-repudiation. These components work together to ensure that information is secure and protected from unauthorized access. It is important for organizations to understand each component and how they work together to ensure optimal protection of sensitive data.